WARNING: YOUR ELECTION RESEARCH HAS DOWNLOADED RANSOMEWARE
by E.A. Jensen and W. Miller
“Because you were logged into your email, you need to pay $99 to fix the hard drive,” said the patient Indian female voice on the phone. Translation: Our computer had been taken over by ransomware.
In working to learn more about the qualifications of judges on the Harris County ballot here in Texas (36 races), we had managed to download ransomeware from one of them. [1]
Harris County stands out in the annals of political science as having the longest ballot in the country. For independent voters who refuse to vote the party line, their duly diligent research to avoid another Judge Pratt [2] and elect the most qualified candidates to office faced an additional jeapordy: hackers.
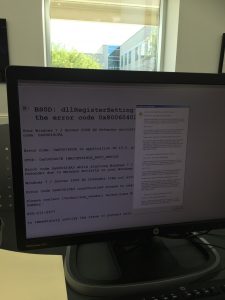
As treasurer of Referee PAC, my researcher (Wanda Miller) and I were tracking down the resumes of these judges to provide independent voters with a 1-stop-shopping location for their qualifications. Using a Lone Star College Cy-Fair campus library computer, we were stunned to click on the website for Jaclanel McFarland (133rd judicial district) and receive a startling error message [3]. On calling the number on the screen, assuming it was from Lone Star College’s IT Department, it took us a few iterations of conversation with the Indian woman on the telephone to realize that (a) she wasn’t with the IT dept (b) she was demanding $99 (c) it came from the candidate’s website and (d) despite all the current issues with Russia, this woman was definitely not talking with a Slavic accent.
Hacking activity is at a frenzied pace this year. Yahoo admitted to being “pwned” in 2014, the Democratic National Committee’s internal server was compromised, and even Mark Zuckerberg’s (Facebook) Twitter account was hacked. It’s inevitable that the website created by a candidate’s most computer knowledgeable friend is going to be lacking in rigorous computer safety protocols. Under these conditions, our election process makes for an easy target. The situation is further complicated by (a) voters who are trying to conduct research as their civic duty with no central location to turn for down-ballot information (b) software that detects compromised websites are not at the 90% threshold [4] and (c) there is no organization to which to turn for monitoring the situation.
On realizing that we had opened the community college campus’ computer system to ransomware, we pulled the ethernet cable and reported it. However, given the potential threat to our election system that had just been demonstrated, that wasn’t enough. Who do we tell that there’s a serious threat facing our democracy if voters don’t feel safe looking up information on candidates from their websites? Having attended a safety meeting in which the precinct’s constables indicated they were building a strong IT presence, I called them for assistance on what to do. The response was: “go talk to the website’s owner.” The problem with the next stage solution they offered was that I couldn’t look up the candidate’s contact information without their website. In the end I called the county’s Democratic headquarters and left a message.
A week later, we came upon a very suspicious Republican website, Republican candidate for 215th judicial court Fred Schuchart [5]. Leery of another compromised machine, I called the county’s Republican headquarters and left a message.
Neither HQ has called me back. [6]
References:
[1] http://www.techrepublic.com/article/no-more-ransom-takes-a-bite-out-of-ransomware/
[2] http://www.chron.com/news/politics/houston/article/Embattled-judge-Pratt-resigns-suspends-campaign-5358490.php
[3] https://refpac.org/wp-content/uploads/2016/09/IMG_5736rot.jpg
[4] “Google was able to blacklist 52 per cent of the compromised sites found while Norton Safeweb managed to find 38 per cent and McAfee SiteAdvisor found only a disappointing 11 per cent of the hacked sites.”
http://www.itproportal.com/news/16000-wordpress-sites-hacked-so-far-this-year/
[5] Steps to research safely.
Step 1: Install a tor browser on your machine (torproject.org). It’s very restrictive on permitting software to be downloaded to your machine.
Step 2: search for candidate websites through tor. If a loading problem occurs, do the following tests.
Test A: open google translate’s website and enter the web address of the problem website. If you continue to get an error (beyond the “page is already in English, load the original”) perform the next test.
Test B: go to https://sitecheck.sucuri.net// and enter the website. If it shows a green check button, make sure that it doesn’t show a website loading error. If it shows a website loading error (with a green button) or a red alert symbol, then the website is possibly compromised. DO NOT LOAD IT.
Step 3: Feel free to let us (Referee PAC) know about the website. We’ll notify the appropriate party.
[6] It’s been my experience that HQ is not very responsive and that one needs to contact their local Precinct Chair in order to get something done.
